Protecting Financial Data from Ransomware: What Small Businesses Need to Know
Reading Time: 7 minutesRansomware attacks aren’t just hitting big corporations anymore. Today, small businesses are right in the crosshairs.
Why?
Because your financial data is just as valuable, but often less protected.
And here’s the kicker.
Most small businesses don’t have the resources to recover from a breach. That’s why smart cybersecurity practices and secure financial tools like Akaunting are vital. With the right protections in place, you can significantly limit the chances of a ransomware attack.
Let’s take a closer look at what ransomware is, why attacks are skyrocketing, and how to protect your small business from financial chaos.
Table of Contents
- What’s Ransomware?
- Why Is It More Important Than Ever to Protect Financial Data from Ransomware?
- 5 Ways Small Businesses Can Protect Sensitive Data from Ransomware
- Wrap Up
What’s Ransomware?
Ransomware is a form of malicious software.
Sometimes known as data extortion, ransomware encrypts your data, locking you out of your own systems, until you pay a ransom. Sometimes, hackers even steal the data and threaten to leak it online. (This is known as double extortion.)
If you don’t pay up on time, these cyber criminals will delete your data, sell it on the dark web, or leak it to the public.
And what makes ransomware really dangerous to small businesses is how quickly it can get in — and how far it can spread once it’s inside.
Let’s break it down.
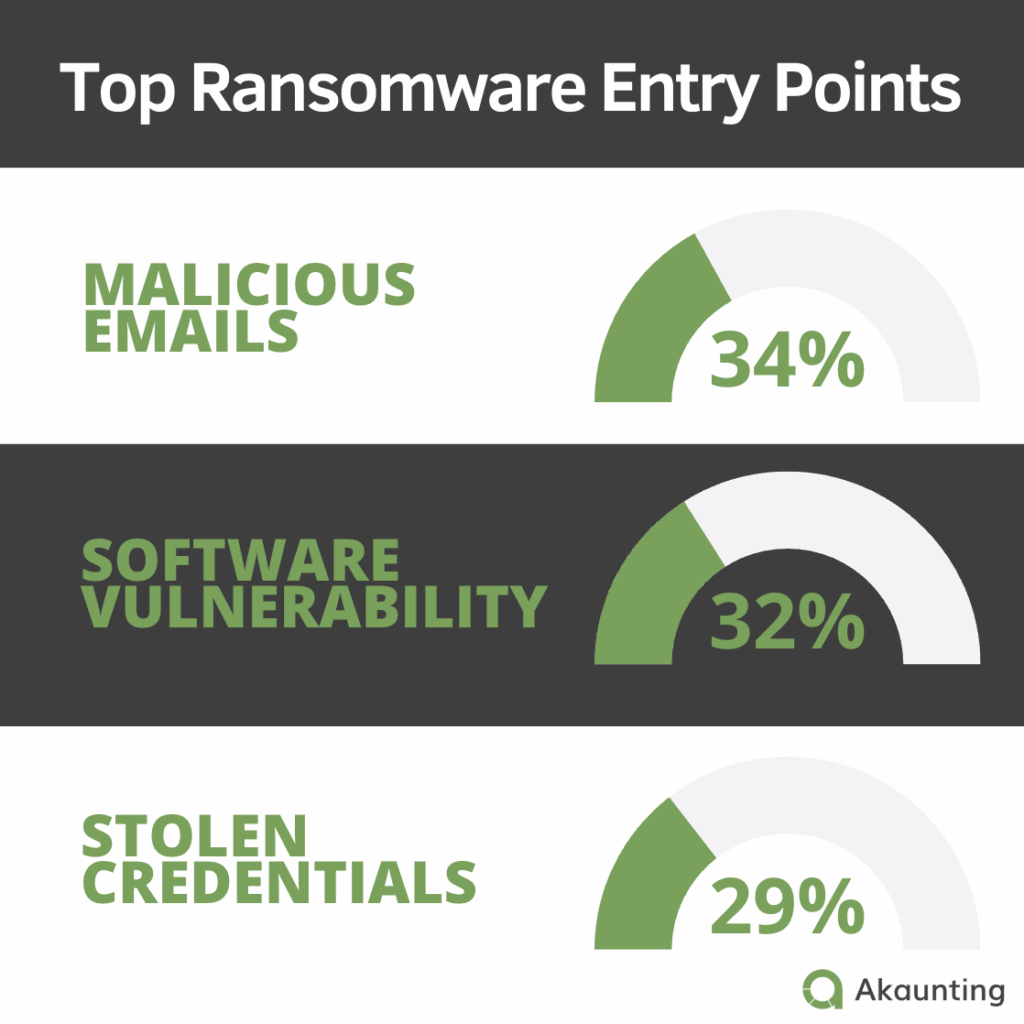
Most attacks don’t start with some genius hacker writing code from scratch. They start with something simple:
- – 34% of the time, an employee clicks a suspicious link in an email
- – 32% of cases come down to software vulnerabilities, usually due to a late update
- – 29% of breaches come from stolen admin credentials
(Image made by Ioana)
It’s a perfect storm. Easy access, valuable data, and weak defenses.
And once inside, the ransomware doesn’t encrypt a few files. It spreads quickly through your system.
➜ Without strong access controls and proper network segmentation, attackers can lock down your entire system in minutes.
But why are small businesses an especially easy target?
There are several reasons why ransomware attackers target small companies as low-hanging fruit. Specifically:
- – Supply chain attacks: You’re often connected to other small vendors and platforms. This is a ripe opportunity for hackers to get in through other connected systems.
- – Local storage: Sensitive information, such as tax records, payroll data, and payment details, is often stored locally on office or home devices.
- – Poor security: You may not have a dedicated IT or cybersecurity team to keep systems patched and monitored.
- – Remote work: You might have a hybrid or remote team, which introduces unsecured personal devices into the mix.
- – Legacy tools: You may be running outdated software, riddled with bugs, and lacking the latest security patches.
- – Value: Your customer and financial data is just as valuable as data from a big enterprise. (And easier to steal.)
And when you mix all of that with today’s hyper-sophisticated ransomware kits and marketplaces?
It’s open season.
Why Is It More Important Than Ever to Protect Financial Data from Ransomware?
Let’s not sugarcoat it. Ransomware is exploding. And it’s not slowing down … it’s evolving.
In 2023 alone, 69% of businesses were hit by ransomware attacks.
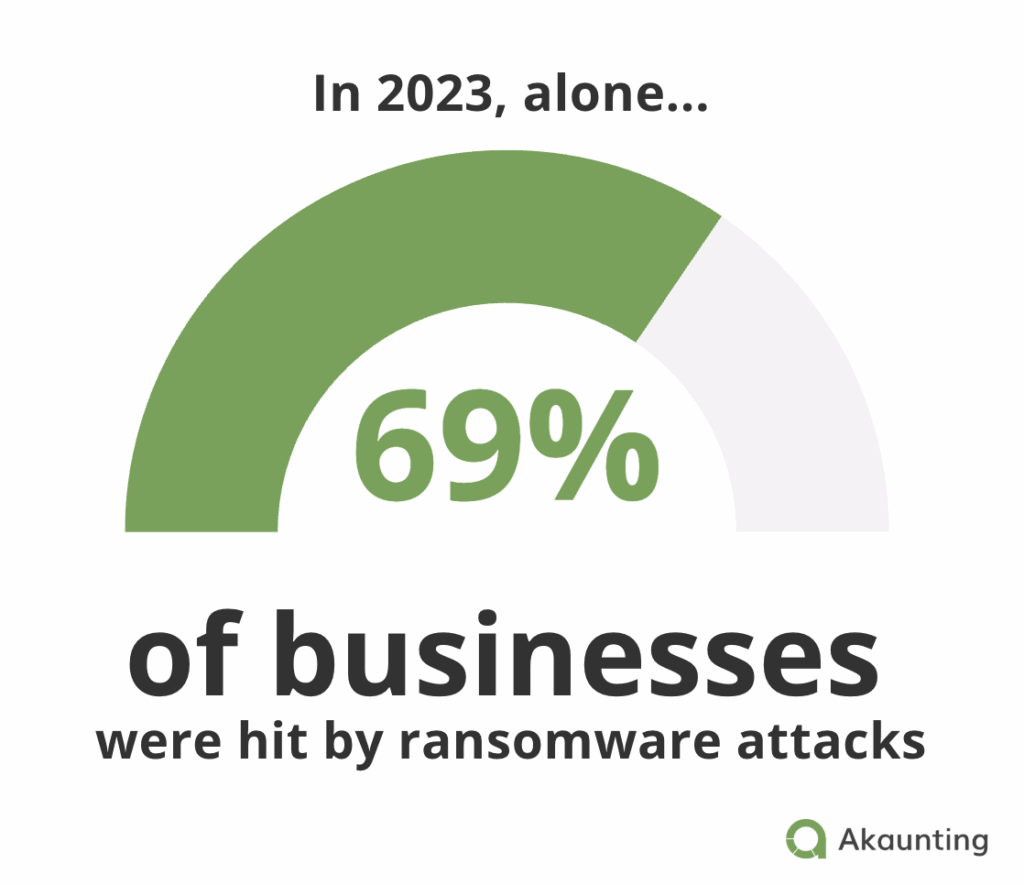
Image made by Ioana
But why has ransomware become so prevalent?
Here’s why:
Attack Surfaces Are Growing
Today’s small businesses often run on third-party platforms, cloud storage, and digital workflows.
While this is highly convenient, it expands your attack surface. The more tools, devices, and platforms you use, the more entry points hackers have to get in.
And it’s not just your systems you have to worry about. Attacks are now also occurring through supply chain vulnerabilities. So if your payroll platform or software vendor is breached, you could get caught in the crossfire.
This is why it’s so important that small businesses that use cloud services adopt a Cloud-Native Application Protection Platform (CNAPP) to defend their operations against ransomware.
AI, Phishing, and Deepfakes Are Getting Smarter
Thanks to artificial intelligence (AI), attackers now create hyper-realistic phishing messages to trick employees. This includes emails, voice messages, and videos (often impersonating someone internal).
And remember, malicious emails are the most common way attackers get in. So if your team isn’t highly trained at spotting phishing attempts, they’re your weakest security link.
Ransomware-as-a-Service
With Ransomware as a Service (RaaS), criminals don’t even need to know how to code. They simply buy attack kits online and deploy them like a subscription.
That means more attackers, more tactics, and more cyber threats — especially for businesses without dedicated cybersecurity teams.
5 Ways Small Businesses Can Protect Sensitive Data from Ransomware
You don’t need a massive security budget to protect your business. But you do need the right layered strategies combined with the right software.
Here’s what to focus on to protect your financial data from ransomware.
1. Use Cloud-Based Tools That Minimize Local Vulnerabilities
Local storage is easy to encrypt, wipe, or steal. So if your financial data lives on your laptop or desktop, it’s vulnerable. All it takes is one infected file, and you lose access to everything.
And unless you have a clean, recent backup stored somewhere safe, it’s game over once ransomware hits.
That’s why moving financial data and customer details to the cloud matters.
Cloud-based tools don’t rely on the security of your local machine. Instead, your data lives off-site. It’s secured in professionally maintained environments that are designed to resist cyberattacks.
Take Akaunting, for example.
Akaunting is a fully cloud-based accounting and payroll platform. That means your financial data is never stored on local devices where ransomware can reach it easily.
Instead, everything is stored on Akaunting’s secure, encrypted servers, protected by continuous monitoring and modern cybersecurity protocols.
Even if your laptop is compromised, your data is still safe and accessible from another device.
What’s more, Akaunting’s cloud platform is constantly updated to patch security vulnerabilities behind the scenes. So you never have to worry about outdated software creating risk.
2. Create a Backup Strategy
No backup copy of your data? Then you won’t be able to recover it if a hacker locks you down.
Without data backup, ransomware wins. Once they’ve locked your data down, you have no choice but to pay the ransom to get it back. If they even give it back.
With a clean backup, you can simply wipe the infected machine and restore the system using the backed-up data.
Try the 3-2-1 backup rule: Three copies of data, two different formats, and one offsite.
Or even better, the 3-2-1-1 strategy. That’s three copies of data, two different formats, one offsite, and one air-gap backup (disconnected from the internet).
Sounds simple, right?
However, in practice, many small businesses skip this step because manually managing backups is a hassle. It takes time, planning, and often, extra costs.
That’s why your financial software must offer built-in backup protection.
Akaunting does just that.
It supports cloud-based backups, automated scheduling, and secure off-site storage. So even in a backup attack scenario, you’ve got a clean version of your financial data ready to restore.
3. Encrypt Everything in Transit and at Rest
Encryption is the process of scrambling your data so that only authorized users with the right key can read it.
Encryption in transit means it’s protected while being transferred (like during uploads). And at rest means it stays protected while it’s stored.
This process is crucial because it ensures that even if your data is stolen, a hacker can’t read or use it. Without the decryption key, it’s useless.
Secure financial tools like Akaunting utilize end-to-end encryption — both when your data is stored and when it’s in transit.
This is one of the most effective cybersecurity practices out there. Apart from stopping hackers from using it, it also protects you from double data extortion incidents. Hackers won’t be able to leak or sell it because it’s unreadable.
4. Control User Access and Track Activity
A shocking number of attacks happen through unauthorized access to employee accounts.
But the entry point is just the beginning.
If you don’t have strong access controls in place, that one stolen password can open the door to your entire system. Hackers can move laterally — snooping, encrypting, and stealing data across multiple accounts before you even notice.
That’s why strong access controls are essential.
Here are a few important access control tactics to use:
- – Multi-Factor Authentication (MFA): MFA requires users to prove their identity with a second method (like a text code or face ID). Even if a hacker steals a password, it’s not enough to get in.
- – Role-Based Access Control (RBAC): RBAC only gives people access to the data they need. So, even if a hacker steals someone’s credentials, they’re limited to the parts of the system that user was allowed to access.
- – Custom User Permissions: Custom permissions fine-tune what each team member can view, edit, or delete. That way, sensitive financial data isn’t floating around freely.
- – Automatic Audit Logs: Logging tracks every login and action taken in the system. This helps you identify suspicious activity quickly and prevent it from causing significant damage.
Together, these controls limit what hackers can touch, even if they do get in.
Akaunting offers all of these safety nets.
You can assign user roles, set detailed permissions, enable MFA, and monitor login activity — all from your dashboard.
5. Validate Your Security
Cybersecurity isn’t a set-it-and-forget-it exercise.
You can’t simply install antivirus or enable MFA and rely on it working. Cybersecurity tools are only as good as their configuration and hackers are counting on you never testing them.
This is where security control validation becomes super important.
Security control validation involves verifying that all of your defenses function as intended. You check your firewalls, endpoint protection, data encryption, access controls, etc. to identify gaps before attackers do.
You can even use a security control validation tool to simulate attacks and uncover weaknesses across your systems.
Pair this with:
- – A basic cybersecurity assessment tool
- – An incident response plan
- – A disaster recovery plan
➜ This gives you a real foundation for staying resilient against ransomware.
Wrap Up
Ransomware is no longer a distant risk for big companies to worry about. It’s a daily threat to small businesses everywhere (especially those with limited cybersecurity resources).
But you’re not powerless.
With good cybersecurity hygiene and secure financial tools like Akaunting, you can:
- – Encrypt everything automatically
- – Store data safely in the cloud
- – Restrict unauthorized access
- – Restore backups in minutes
This is how you defend your business, maintain business continuity, and sleep better at night.
Protect your business with secure, cloud-based payroll and accounting from Akaunting. Try it free today.
About the Author

Kelly Moser is the co-founder and editor at Home & Jet, a digital magazine for the modern era. She’s also the content manager at Login Lockdown, covering the latest trends in tech, business and security. Kelly is an expert in freelance writing and content marketing for SaaS, Fintech, and ecommerce startups.




