Beyond Antivirus: The True Financial Cost-Benefit of Cloud Security for Small Business Data
Reading Time: 7 minutesAs a small business owner, you likely view cybersecurity as an IT issue for large businesses.
However, small businesses are often the easiest targets, so having cybersecurity features in place is important.
Your antivirus software isn’t enough to hold attackers back, especially in today’s cloud-dominated software-as-a-service (SaaS) space. Antivirus software just isn’t built to protect your data once it leaves your desktop.
The conversation about cloud security for small business data has been dominated by the IT industry for too long. We need to reframe it for what it really is: a core financial decision. This post breaks down the true cost-benefit analysis of cloud security, moving beyond technical specs to focus on the only metric that matters to you: your bottom line.
The hidden price tag of a cloud data breach
So, what’s data breach?
For a small business, a security incident can be a significant financial liability that persists for years. Before we analyze the benefit of security, let’s establish the high cost of doing nothing.
According to IBM research, the global average cost of a data breach in 2025 is set to reach $4.44 million. But that’s just the average. The cost depends strongly on the industry or sector you operate in.
Today, even a small breach can easily result in potentially hundreds of thousands of dollars, a sum that could bankrupt many small and mid-sized businesses.
But where exactly do those costs come from?
The direct costs of a security incident
These are the immediate, out-of-pocket expenses you’ll face as soon as a breach is discovered. They include:
- – Forensic investigation: You have to pay experts to figure out what happened, how they got in, and what unauthorized access they gained.
- – Regulatory fines: In 2025, 32% of all breaches involved regulatory fines. These fines depend on your industry and location.
- – Notification and support: You are legally required to notify customers whose data was compromised and pay for ID protection and credit monitoring services for every affected person. These costs can represent as much as 8.8% of the total.
The compounding interest of a damaged reputation
This is the cost that lingers. It’s the lost business category from the IBM report, which includes revenue lost to:
- – Reputation damage
- – Lost customers
- – Downtime
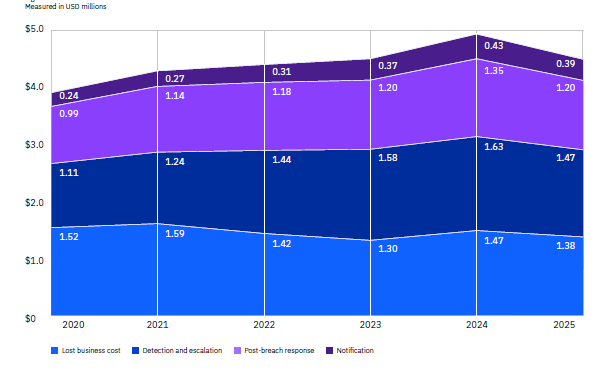
Every minute your systems are offline, you are losing money. You can’t access your Microsoft 365 files, Google Workspace, or cloud accounting software. Your business accounts are frozen, and you’re hemorrhaging cash. For small businesses, even short-term downtime can cripple operations and lead to cascading losses — from missed client payments to damaged trust.
Why your cloud provider won’t cover your losses
Here is one of the most expensive assumptions a business owner can make:
My data is in the cloud, so my cloud provider is responsible for securing it.
This is fundamentally wrong.
All major cloud computing platforms, including Amazon Web Services (AWS), Microsoft Azure, and the Google Cloud Platform, operate under a Shared Responsibility Model. In short, they’re responsible for the security of the cloud:
- – The physical data centers
- – The core network
- – The servers
You’re responsible for the security in the cloud. This includes your:
- – Identity and access management data (i.e., who has the keys)
- – Applications and software
- – Customer data
- – Business data
In short, you’re still responsible for managing user access, defining roles and permissions, preventing account hijacking, and securing the data you store. For example, if an employee uses a weak password and a hacker logs into your cloud account, that’s your liability, not the provider’s.
Analyzing the investment: What are you actually paying for in cloud security?
Now that we understand the catastrophic cost of a breach, let’s reframe cloud security as a smart investment. You’re not buying tools; you’re buying risk reduction.
The foundational security measures and their (surprisingly low) cost
You can eliminate the vast majority of your risk with a few foundational security measures that cost little to nothing:
MFA protection
Multi-factor authentication (MFA), of which two-factor authentication (2FA) is the simplest form, is the single most effective control. It’s free and built-in on most services, including Google Workspace, and only incurs a minor fee in others, such as Akaunting’s cloud service.

Password management
A password manager creates unique, complex passwords for a few dollars per user per month. It’s a small investment that prevents employees from setting weak or reused passwords, avoiding a massive risk.
Data Encryption
Modern cloud solutions automatically use AES-265 encryption to protect your data at rest. Some use the same level of encryption to protect data in motion. Your only job is to ensure it’s turned on.
When to invest in advanced security controls
As you grow, you need to control who can access what. This is identity and access management (IAM), and its goal is to provide least-privilege access, meaning employees only have the exact access they need.
As your cloud environment grows, you must complement IAM with cloud infrastructure entitlement management (CIEM).
CIEM security helps you right‑size cloud permissions and cut risks you’re probably blind to. CIEM avoids an attacker draining your data or budget after compromising an account by:
- – Mapping every human and machine identity
- – Granting time‑bound access to users
- – Striping standing admin rights

The payback shows up in fewer incidents, cheaper audits, and lower premiums because you can prove least‑privilege by design.
The cost of training vs. the cost of human error
Human error is the root cause of over a quarter (26%) of all data breaches.

Screenshot provided by author
Your security is only as strong as your team. The cost of a 30-minute training session on spotting phishing emails is nothing compared to the massive, uncapped financial risk of one accidental click.
The tangible ROI of strong cloud data security
Good security isn’t just a shield; it’s a business enabler that actively contributes to your bottom line. This is the indirect benefit side of the cost-benefit analysis.
Unlocking new business: Using security as a sales tool
Strong security is a competitive differentiator. As you pursue larger clients, they will vet your security practices. Being able to confidently present your security policies, MFA protection, and compliance features (like alignment with ISO 27001) can be the single factor that makes them choose you over a competitor.
Lowering premiums and demonstrating due diligence
Cyber liability insurers are now demanding strong security controls before offering a policy. Implementing these basics makes your business insurable and can significantly lower your premiums. It also proves due diligence, limiting your liability in a legal dispute.
A practical cost-benefit action plan for your small business data
Here is a practical, three-step plan you can start today.
Step 1: Conduct a 60-minute data classification audit
You can’t protect what you don’t know you have. Ask these questions:
- 1. What data do I have? (e.g., customer PII, financial reports).
- 2. Where is it? (e.g., Akaunting cloud account, Microsoft 365, local laptops).
- 3. Who has access to it?
This simple act of data classification is the free, essential first step in a zero-trust security model.
Step 2: Prioritize the low-cost, high-impact security measures
Using the audit from Step 1, take the necessary action.
- – Today: Enable MFA protection on all your cloud accounts, your email, and your bank login for all users.
- – This week: Sign your team up for a password manager, mandate its use, and change all current passwords to unique and stronger ones.
- – This month: Review all user permissions and remove admin rights from everyone who doesn’t absolutely need them.
Step 3: When to manage it yourself vs. calling in an expert
You’ve now handled 80% of the risk. Now, analyze the cost of your time. Is it better to become a cybersecurity expert or run your business?
For most SBOs, the answer is obvious.
Partnering with a managed security service, such as Vigilant Technologies, offers small businesses significant financial advantages. Vigilant Technologies provides advanced cloud security solutions, including:
- – Automated vulnerability assessments
- – Real-time threat monitoring
- – Secure data backup
These solutions mitigate expensive breaches, enhance operational efficiency, ensure compliance, and build customer trust. By utilizing these services, businesses can safeguard their data, mitigate financial risks, and concentrate on driving growth.
The final calculation of cloud security for small business data
Your old antivirus software was designed to protect one computer. Cloud security is designed to protect your entire business—your revenue, your reputation, and your customers’ trust.
The financial case is clear. The cost of a data breach is unpredictable and catastrophic. Investing in smart cloud security for small business data is predictable, manageable, and yields a clear, positive ROI.
Protecting your financial data is the first step. Then you also need to know how to manage it effectively. Now that you know how to secure your business, take control of your books with a tool that’s just as smart, simple, and secure.
Try Akaunting’s free cloud-hosted accounting software today.
About the Author

Kelly Moser is the co-founder and editor at Home & Jet, a digital magazine for the modern era. She’s also the content manager at Login Lockdown, covering the latest trends in tech, business and security. Kelly is an expert in freelance writing and content marketing for SaaS, Fintech, and ecommerce startups.



